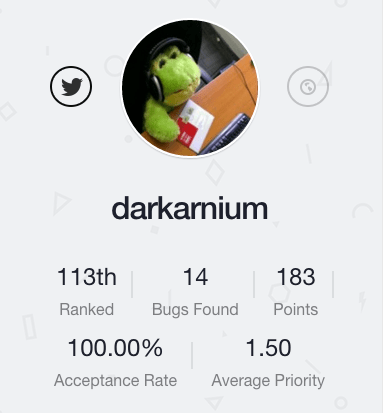
It’s only been 5 months since Darkarnium joined Bugcrowd, but in that short time he’s shot his way up our all-time leaderboard to #113 and impressed us all with his 100% acceptance rate and 1.5 average priority. Darkarnium is a bit of a “sniper”, the bugs that he submits are often a high priority and high impact.
We recently caught up with Darkarnium for this week’s Researcher Spotlight. He’s one of the fast rising stars in the bug bounty researcher community, and we’re excited to have him at Bugcrowd.
You can follow Darkarnium on Twitter @Darkarnium and check him out on Bugcrowd.
Q: How did you get started in security research? How long have you been doing bug bounty work?
A: I’ve had a passing interest in embedded device and web application security for some time, but I never really went past reading papers and advisories until earlier this year.
The interest in the former I think started as a natural extension of the need to rip apart any new hardware I got my hands on and poke around at the internals. It wasn’t long before it turned into a more black-box style game of ‘can I get a root shell on this device without cracking the case?’
As for participating in bounty programs, I sort of ‘fell’ across a few programs earlier this year and decided to give them a shot. Through sheer dumb luck, I found a couple of vulnerabilities in a product which were confirmed by the provider quite quickly and patched not long afterwards. From there, it has escalated into more of a hobby than anything else, consuming far more of my time than I would have imagined even 10-months ago.
Q: Do you have a specific focus or specialty that you tend to spend your time on?
A: I still try and focus on hardware as much as possible, but It’s good to have some variety. Sometimes you just don’t feel much like waiting for the fifth ‘vagrant up’ of the evening to complete so that you can finally get an image compiled with the RIGHT incantation this time 🙂
Q: What motivates you to do what you do? What keeps you going?
A: A lot of the time it’s the ‘thrill of the chase’, trying to see whether you can persuade an application into doing something it perhaps wasn’t designed to do; for better or for worse. Trying to turn a seemingly innocuous vulnerability into something more drastic using the information or access you’ve managed to garner thus far.
It’s also always interesting trying to decide whether to keep testing, write up any issues found, or go to bed at two o’clock in the morning, but somehow, you find yourself doing the same damned thing 24 hours later.
Q: Any tips or suggestions that you would give to other bounty hunters?
A: LinkedIn profiles, company ‘careers’ pages and public mailing lists are your friend! If you want to know what you’re likely to encounter in a given stack, see what sort of developers, QA and operations skill-sets a company is employing.
A quick search for posts to public mailing lists from ‘corporate’ email addresses can also greatly help your understanding of the tools an organization has used to build / deploy their application as well. Sometimes you’ll get really lucky and end up with otherwise unpublished URLs that are in-scope running code that hasn’t been hardened as much as more ‘public’ services.
Finally, get more sleep! If you’re working on a problem that you’ve been working on for a few hours, take a break and come back to it after you’ve had a moment to collect your thoughts 🙂
Q: What do you think of the future of bug bounties? Where do you see them going, where would you like to see them go?
A: There seems to be more organizations running bounty programs in some form recently, which I see as a huge positive for researchers, the organizations themselves and as a result their customers. I’d like to think that the successes of these programs will drive more organizations to participate, but I suppose we’ll see what happens.
As for where I’d like to see them go? I’d love to see more ‘wildcard’ scoped programs. There’s not much point in making sure your primary web application is bullet-proof, only to find that there’s a fat-fingered ACL on your border exposing other more sensitive components of your network to the internet.