In the past year, the U.S. Federal Trade Commission (FTC) and Department of Justice (DOJ) have released guidance outlining the need for vulnerability disclosure programs (VDP). With support from major legislative bodies like the National Institute of Standards and Technology, widespread adoption of vulnerability disclosure programs is expected and necessary in the coming years.
In this post, we will explore what a vulnerability disclosure program is, why they’re a bit more complex than you might realize, and identify some things to consider when adopting your own.
What is a vulnerability disclosure program?
A vulnerability disclosure program offers a secure channel for researchers to report security issues and vulnerabilities, and typically includes a framework for intake, triage, and workflows for remediation.
To better illustrate, let’s use a concept that you’re probably already familiar with, “neighborhood watch.” A neighborhood watch encourages people to report something if they see suspicious activity. Using this analogy: if you saw your neighbor’s front door open, you would probably want to let them know about it.

Figure 1: Security breach identified by 3rd party
But if you didn’t already have your neighbor’s contact information, how would you let them know? Or if you left a note, how will you know if they received the message? Vulnerability disclosure programs provide a way to report potential security risks to your neighbors in a formalized and consistent way, but also provide a channel for the reporter to be notified you got the message. Now let’s think about this in terms of your internet-facing assets.
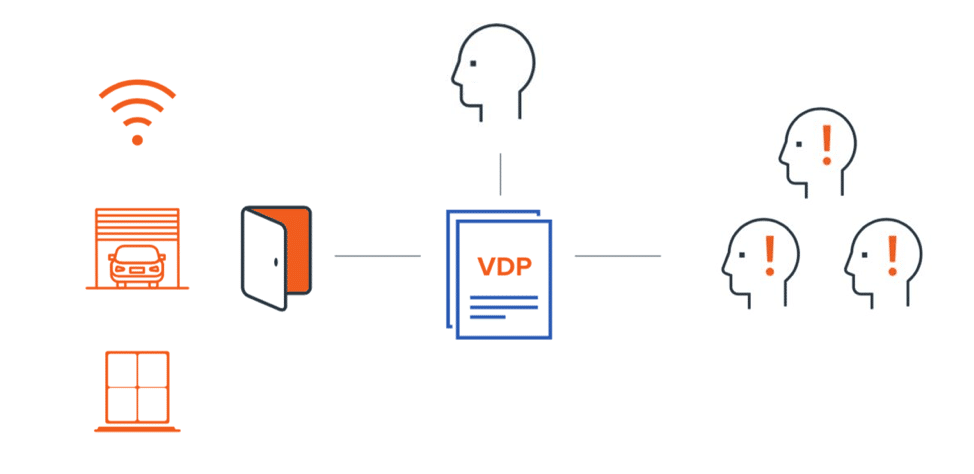
Figure 2: VDP as a neighborhood watch
You and your neighbors have an easy way to communicate with each other in the event you find a security risk. And this is not limited to just an open door – it could be an open window, garage door, or even a Wi-Fi connection without a password. With a vulnerability disclosure program, researchers and companies can send and receive vulnerability reports in one central channel.
Major companies like Walmart, Office Depot, and Motorola Mobility actively use vulnerability disclosure programs to provide a submission channel to the wider researcher community. At the same time, having a vulnerability disclosure program tells customers you care about their security.
So it seems like common sense right? Why wouldn’t you want good neighbors to let you know when something looks broken?
The hard part of vulnerability disclosure
Your neighbors are not perfect. Some of them might be a little too cautious, and assumed your window was open when it really wasn’t (that Windex works!). Or, perhaps it could be that you actually have guest Wi-Fi on top of your private network.
As your house or “organization” increases in size, and your potential attack surface increases, inherently increasing risk and the number of security vulnerabilities. Managing these incoming reports can easily turn into a nightmare, inundating your security team with vulnerabilities.
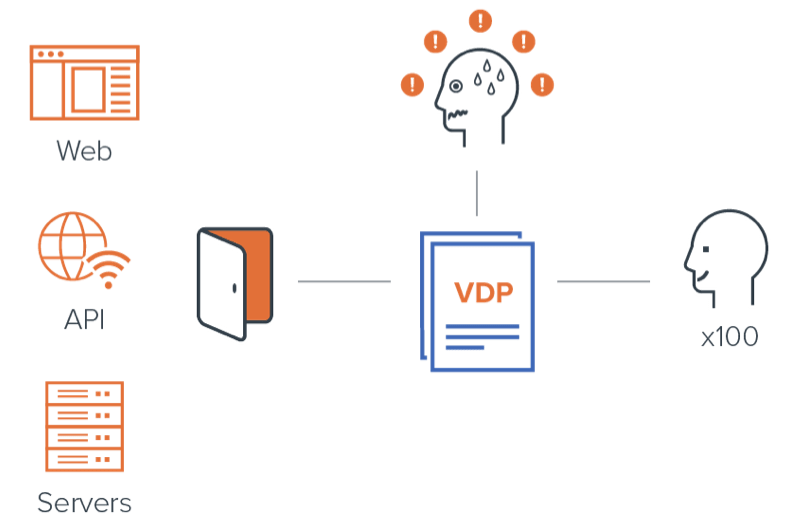
Figure 3: Influx of vulnerabilities at scale
What’s needed at scale is a way to triage the reported security risks coming in from researchers, and to prioritize the security risks that matter. Organizations do not have the time or resources to triage and validate every single incoming finding. It is vital to designate a key stakeholder, team or partner to provide management, including technical review and escalation of valid vulnerability submissions as well as facilitation of researcher communications crucial for detailed reports, deeper context, and high engagement.
Bugcrowd’s fully-managed vulnerability disclosure programs
Bugcrowd provides a framework to securely accept, triage, and rapidly remediate vulnerabilities submitted from the global security community, all from our all-in-one SaaS platform, Crowdcontrol.
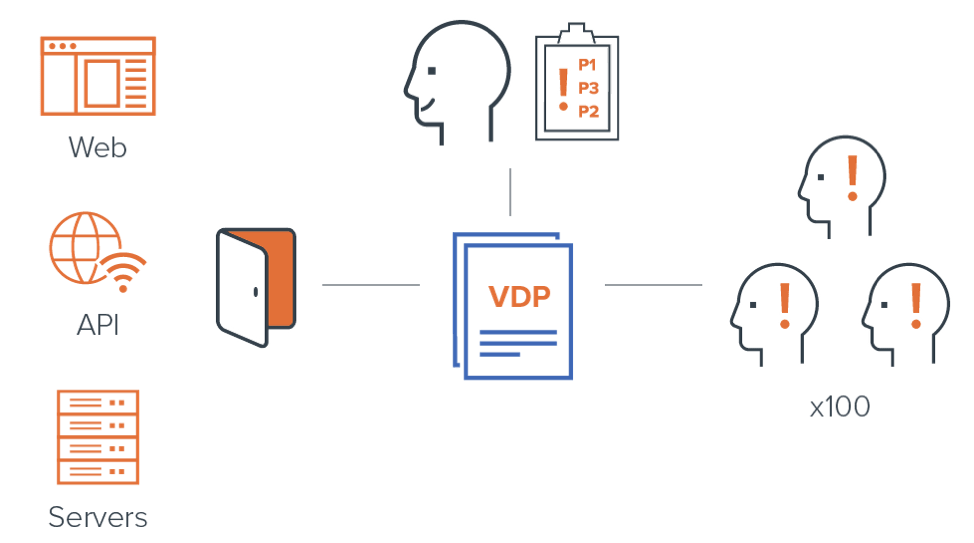
Figure 4: Bugcrowd solves problem of scale
Crowdcontrol, combined with our in-house team of security experts, facilitates hundreds of managed vulnerability disclosure programs, escalating high-priority issues within hours and averaging triage completion within one business day. This means that all the vulnerabilities coming through the researcher crowd are first vetted by Bugcrowd, according to objective rating standards like our own Vulnerability Rating Taxonomy (VRT).
In short, Bugcrowd removes virtually all overhead for your security team so they can focus on reducing risk by remediating the vulnerabilities identified – making your security team happy and efficient.
To learn more about the additional benefits of a VDP, watch this webinar on Why Every Company Should Have A Vulnerability Disclosure Program with Bugcrowd Founder Casey Ellis and CSO David Baker.
Bugcrowd connects companies and their applications to a Crowd of hundreds of thousands of security researchers to identify critical software vulnerabilities faster than traditional methods. Powered by Crowdcontrol, companies of all sizes can run crowdsourced security programs to efficiently test their applications and remediate vulnerabilities before they are exploited.



