We’re excited to announce a new approach to organizing, managing, and participating in security programs that we believe will dramatically amplify the value that customers and hackers get from the Bugcrowd Platform – and from crowdsourced security, overall!
In response to customer/hacker feedback, and our own observations about where crowdsourced security should go as an industry, we recently enabled what we call Bugcrowd Security Program Management in the platform. (It’s currently available to all hackers and new customers, with availability to existing customers being phased in.)
We believe that this new method resolves several long-standing issues with crowdsourced security platforms. For example:
- For adopters with multiple types of, and/or numerous, programs – and this is increasingly the case in our industry – program sprawl can add overhead and complexity, and data isolation makes it hard to track a unique submission or asset across different iterations of testing.
- Traditional programs are inflexible, with hardwired scope, integrations, and reporting, so it’s hard to implement them in a way that mirrors the business. For example, you may want to launch and manage multiple pen tests for a specific product, release, or business unit exactly the same way, without reinventing the wheel every time.
- When multiple programs are involved, line-of-sight to overall health and ROI can be difficult when reports don’t cross program boundaries.
Bugcrowd Security Program Management not only closes these gaps, but unlocks other improvements to the overall platform user experience for customers and hackers alike.
Let’s dive into some specifics.
Easier organization, management, and scaling
The fundamental principle of Bugcrowd Security Program Management is that programs comprise one or more “engagements” (i.e., VDPs, Bug Bounties, and/or Pen Tests) with interrelated scope, all sharing the same credentials, submissions, integrations, funding pool, and reporting.
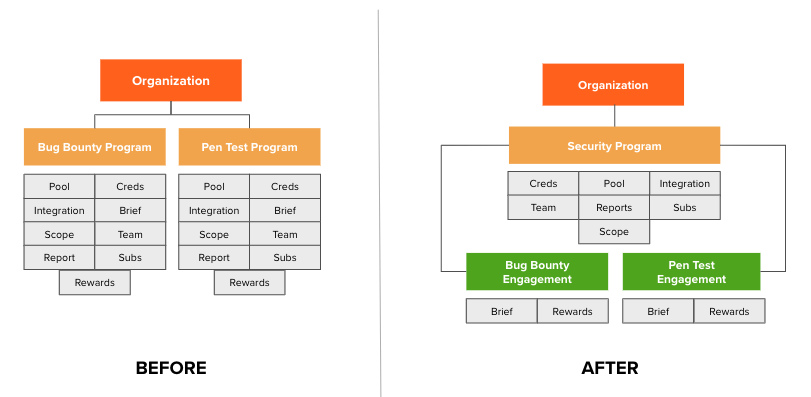
Bugcrowd Security Program Management transforms the status-quo approach, adding greater flexibility and granularity.
This approach has several common-sense advantages, including:
- Customers can meet multiple testing requirements through “hybrid” security programs that, for example, combine engagements for point-in-time, pay-for-effort pen testing and continuous, pay-for-impact bug bounty.
- They can mirror the structure of their own business units, teams, and processes (e.g., for M&A) in the platform while reducing sprawl and overhead, and navigate easily across programs and engagements.
- Moving submissions across programs is rarely needed. Instead, customers can manage a unique submission across multiple assets and engagements, and track the “hardening” of assets over time.
- Cloning engagements for testing at scale is easy. For example, it’s possible to launch and manage a battery of templated pen tests over time, with very little additional setup needed. (This capability has been available in the platform since 2023.)
Richer, more informative briefs
One byproduct of this increased flexibility and granularity is a richer, more customizable brief that is more informative for hackers – contributing to more mutual clarity about scope and targets, stickier participation, and better results.
Enhancements include support for engagement brief changelogs in bug bounty and VDP engagements (already available for pen tests), which document changes to the brief over time. Among other things, changelogs help prevent miscommunications and disputes that may arise when briefs are updated after a report has been submitted.
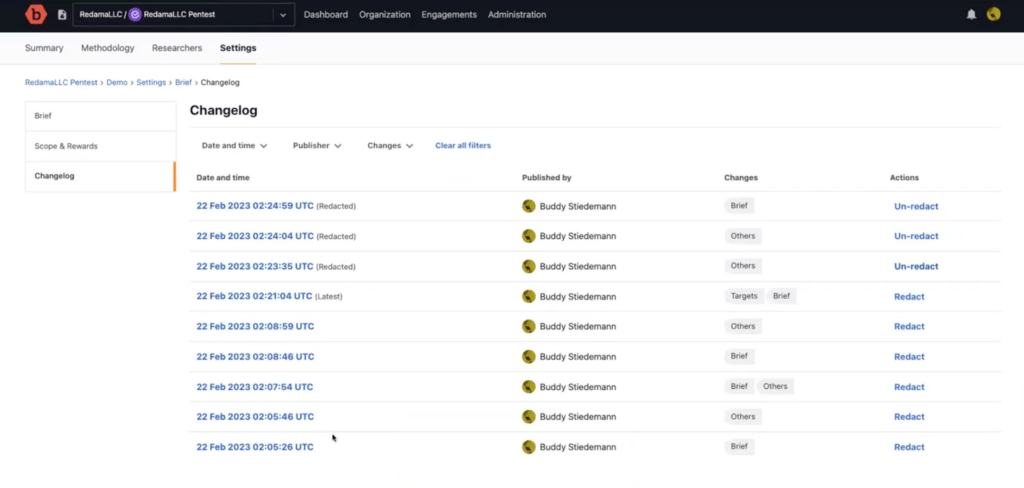
Changelogs can be filtered by time, publisher, and change type.
In addition, a new activity feed in engagement briefs make it easy for customers to communicate and for hackers to see changes to testing dates, targets, scope, and rewards.
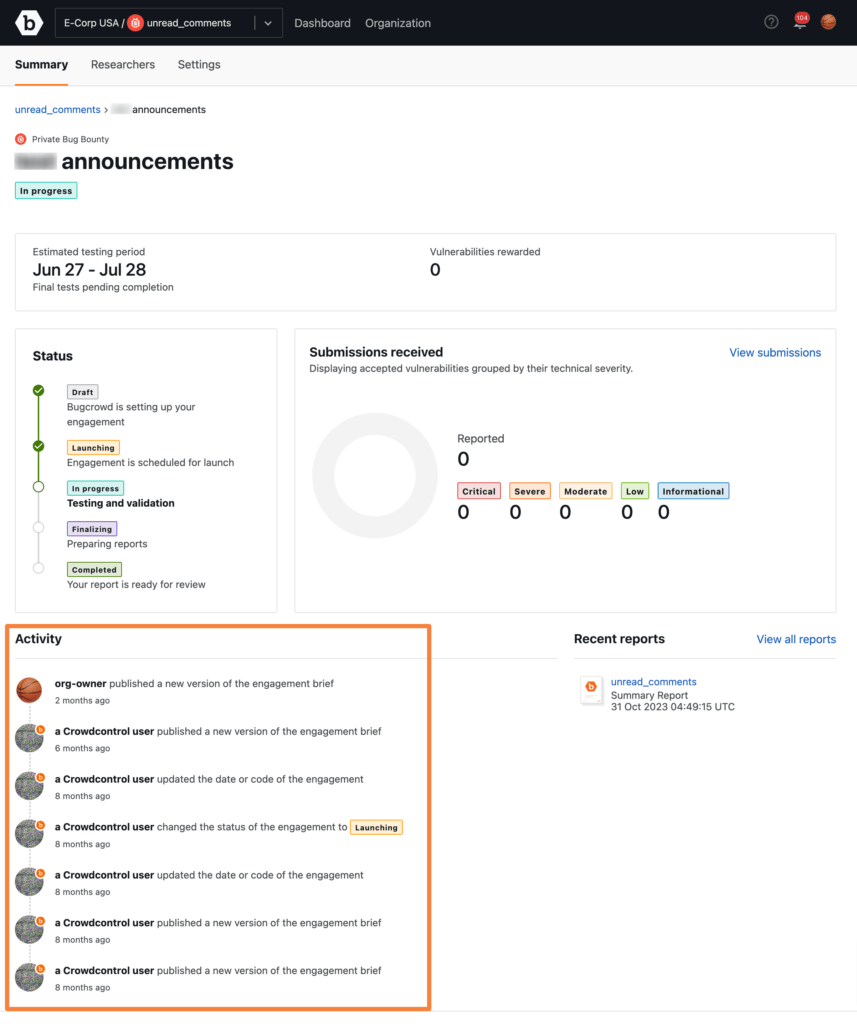
Changes to the brief are displayed in an activity feed.
Customers can utilize more explicit engagement states to accurately share the true state of an engagement as well as the reason for any state changes directly on the brief for improved transparency with the crowd. As well as branded teasers containing scope and rewards data to attract hacker interest without exposing sensitive target details.
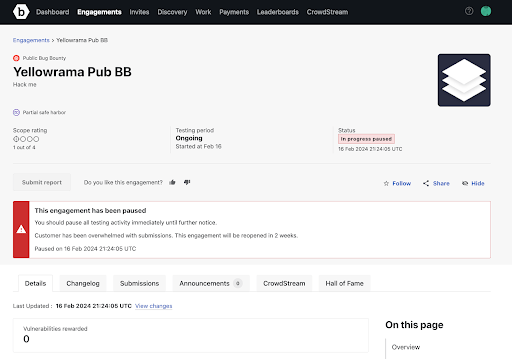
Engagement briefs reflect true state of an engagement and include optional accompanying messaging from customers
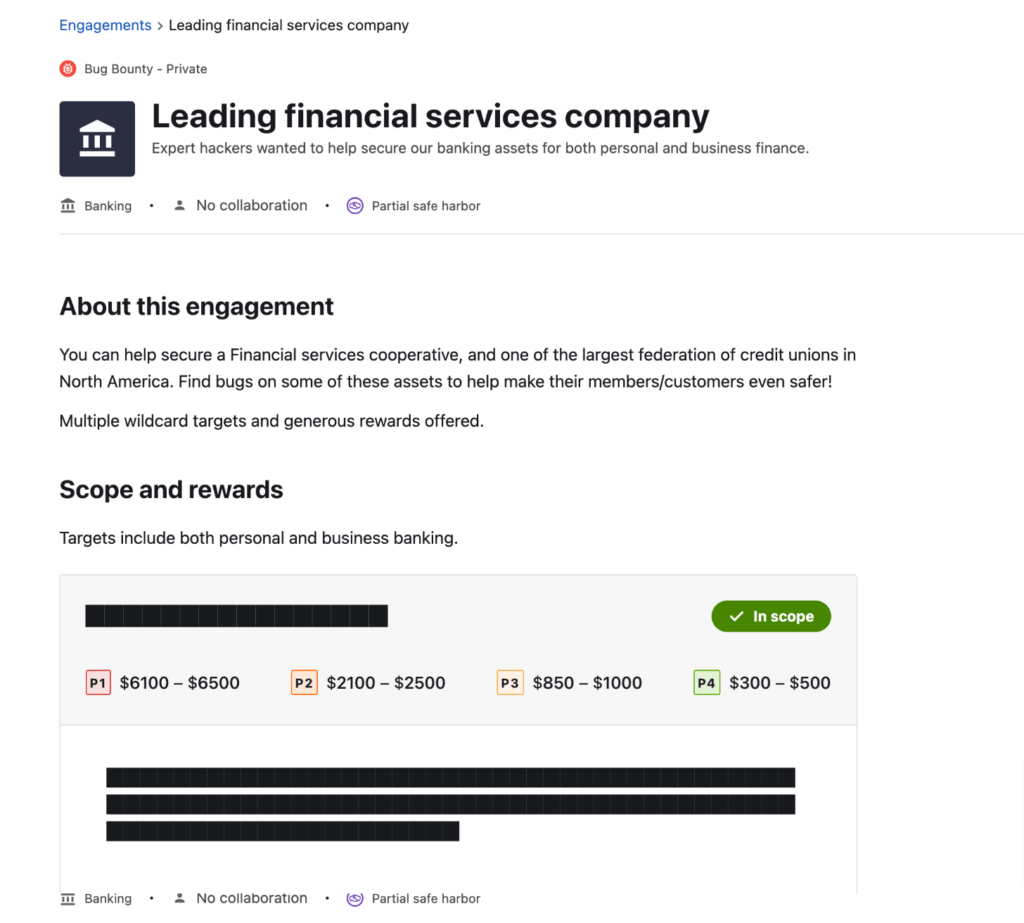
Teasers are now more informative for hackers and can reflect customer branding
Finally, it’s now much easier for hackers to discover new public engagements in the new Engagements index that offer the best opportunities for learning and earning, as well as to understand all the details and current status of those engagements.
Watch this video for a summary of hacker experience improvements; feedback from the hacker community has been solid, so far:
“The new search and filter features make finding opportunities in the Engagements index really easy. In the past, it could be difficult to track down programs that fit the criteria I’m specifically looking for – but now, the ability to select a minimum submission value and filter by feature or focus saves me a TON of time.” – Brandon Reynolds (Hardware Hacker)
Clearer view of health and ROI
Bugcrowd Security Program Management unlocks access to data at a more granular level: reports can now be run across entire programs, on a group of engagements within a program, or on a single engagement. That makes it much easier to understand program maturity and ROI over time.
Next steps
Overall, we’re excited about the positive impact of Bugcrowd Security Program Management on customer and hacker experiences on our platform. And, we’re not done. Look for more announcements soon about how we’re working hard to redefine innovation in crowdsourced security!



