Introduction
We are living in the era of WiFi 6 and WiFi Protected Access version 3 (WPA3). Processing speeds and security technologies over the past decade have improved dramatically. Gone are the days of crackable handshakes and cryptographic vulnerabilities. Nevertheless, the adoption of new security protocols and hardware has remained slow. As a result, many vulnerable WPA2 and open access points (APs) still linger today. In this blog post, we’ll revisit some classic WiFi blasts from the past, talk about cool WiFi recon and hacking tools, and explore how properly implemented WPA3 isn’t hackable—yet. There is very little research on WPA3 security design. However, WPA3 is not as vulnerable as WPA2 to offline brute force attacks, making WPA3 much safer to use.
Types of WiFi attacks
Sniffing
Sniffing is simply the act of listening to the wireless traffic in proximity by placing a WiFi card on “monitoring mode.” Monitoring mode is only supported by certain devices and drivers, but given the right hardware, it can easily be enabled on any operating system with tools like Wireshark and the aircrack-ng suite. USB WiFi cards from Alfa networks and TP-Link Archer series usually do well at monitor mode and packet injection. The same applies to the internal WiFi cards on MacBooks.
Sniffing and decrypting encrypted packets can be performed on WEP and WPA/2 (WPA or WPA2) networks after knowing or cracking the password with tools like airdecap-ng and Wireshark. Of course, for open (non-WPA3) WiFi networks, you can just simply sniff the data packets on any channel and get all network traffic, from DNS and HTTP to encrypted TLS packets.
Injection
The physical layer (layer one) of WiFi is made up of radio waves, making WiFi different from wired networks where one has to be “plugged in” for access. The injection of WiFi management and data packets can therefore be performed easily as long as you are in the transmitting proximity of the receiving device (be it an AP or a client). Tools such as aireplay-ng and bettercap offer mature support for different types of injection.
Depending on the security of the target WiFi networks, injection of management frames can be performed without knowing the WiFi passwords or encryption keys to trick devices into disassociating, deauthenticating, or even joining a new attack-controlled network. The repeat injection of disassociation and deauthentication frames can kick all clients off a network, essentially creating a denial-of-service situation. The injection of data packets such as Address Resolution Protocol (ARP) packets can also be executed on open networks or WPA2 networks with a known password.
Cracking
Older WiFi security standards (WPA2, WPA, and WEP) are vulnerable to offline cracking, as long as you capture the right data via sniffing. For WPA and WPA2, capturing the first two packets in a four-way handshake via sniffing when a new client is joining the network (or rejoining the network after you had kicked them off) is all you need to start cracking.
WPA3 password-protected APs are only vulnerable to online cracking, where the attacker repeatedly authenticates to the AP by guessing passwords in a list. This takes significantly longer and is very noisy but can be done if the password is weak enough.
Rogue AP
Anyone, including attackers, can host a WiFi AP. A rogue AP (sometimes called an “evil twin”) can be created to attract clients that are meant to connect to the real APs. The real APs are the ones they have saved on their device via the service set identifier (SSID), which is the name of the AP. This technique can trick the end device to authenticate with real credentials, be it a pre-shared key (PSK) for WPA/2 networks that can be cracked or the Extensible Authentication Protocol (EAP) username and passwords in encrypted or even plaintext form.
Client devices will treat the rogue AP like the real network after authentication and therefore send network traffic that you can mine for sensitive information (e.g., internal company domain names) or manipulate (e.g., impersonating a Windows server to receive NetNTLM credentials). This is especially useful if an IoT device you are testing is trying to connect to the internet and you want to sniff/intercept its traffic to break into the device.
Aircrack-ng suite: The old guard
Aircrack-ng is a large suite of tools for assessing WiFi network security. It’s the most complete tool set of our time and supports all types of WiFi attacks. It comes pre-installed on Kali Linux, which should be run on a physical laptop/desktop (bare metal) with injection-capable WiFi cards or in a virtual machine with a USB WiFi card passed through to it.
To check if your WiFi card is injection-capable, run:
aireplay-ng -9 wlan0
(where wlan0 is the name of your WiFi interface).
Airodump-ng is arguably the most useful tool in the suite; it allows you to sniff all available WiFi frequency channels (via frequency hopping), pick up information about all APs and clients (e.g., SSID, MAC address, channels, and encryption method in use), and so on. It can also detect when a handshake is captured for an AP, letting you know when you can start cracking the password.
When using airodump-ng, make sure to use -w when writing output files:
airodump-ng wlan0 -w capture
The airodump-ng program will keep running and capturing data until you hit Ctrl-C to interrupt the program.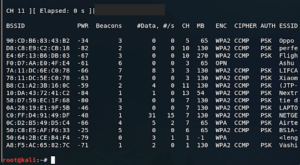
You may want to focus on one specific channel so that you can sniff data from a target AP. For example, if your target AP of interest is on channel 1, you can run:
airodump-ng wlan0 -c 1 -w channel1
This will ensure that you are getting all the data on that channel without losing any during channel hopping, and when new clients authenticate to any APs on that channel, you will receive the handshake.
The aircrack-ng suite also supports injection. You can use aireplay-ng to perform deauthentication attacks on target APs and clients using their MAC address on another terminal window while airodump-ng is running. Running it with just -a to specify the MAC address of the AP will cause it to send deauthentication packets to all clients:
aireplay-ng -0 1 -a 00:11:22:33:44:55 wlan0
For greater accuracy, send deauthentication packets to only a specific connected client (found via airodump-ng) with -c:
aireplay-ng -0 1 -a 00:11:22:33:44:55 -c 11:22:33:44:55:66 wlan0
When the client reconnects, airodump-ng will report that a WPA handshake has been captured, if it’s listening on the right channel.
To crack passwords using aircrack-ng with your CPU (since there’s no GPU support for it), pass it the capture file (and optionally, a wordlist with -w). An example WPA capture file for practice can be found here on the aircrack-ng website.
aircrack-ng -w rockyou.txt wpa.full.cap
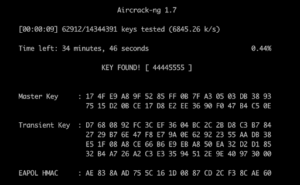
Now that we know the password, we can decrypt any captured encrypted WPA packets after the point of the handshake in the capture file using airdecap-ng:
airdecap-ng -p 44445555 ./wpa.full.cap -e teddy
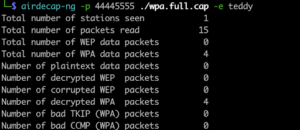
The decrypted packets will show up in wpa.full-dec.cap. This is especially useful in scenarios where you want to see plaintext traffic flows in a WiFi network (e.g., DNS requests and HTTP packets).
Bettercap: The new Swiss army knife
Bettercap is a newer suite of network hacking tools for WiFi, Bluetooth, IPv4, and IPv6. It supports WiFi sniffing and newer injection attacks, such as PMKID-based clientless attacks on vulnerable WPA/2 APs to obtain key material for cracking passwords. It’s available on Windows, Linux, and Mac. Good news for Mac users: it also works on Apple silicon, which we tested to ensure it has monitor mode and packet injection support. Just install it with Homebrew by running brew install bettercap.
You can start bettercap with the interface name specified with -iface. Then, when the bettercap console pops up, you can type in wifi.recon on to start sniffing packets and discovering APs:

To focus on one channel, run wifi.recon.channel <channel>, such as wifi.recon.channel 1. By default, when bettercap picks up any WPA handshakes, it will be saved to ~/bettercap-wifi-handshakes.pcap.
You can list the APs found by running wifi.show:
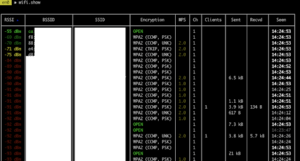
Injection attacks, such as associating to APs to obtain crackable PMKIDs, can be done with wifi.assoc all for all found APs:

For other attacks, including deauthentication and rogue AP, check the help page in bettercap’s WiFi module.
WiGLE: Worldwide wireless reconnaissance
Ever wondered how many wireless hotspots/APs there are in a particular area in the world? Have you been curious about what SSIDs, MAC addresses, and encryptions are used for each one? Look no further than WiGLE.net for worldwide wireless recon.
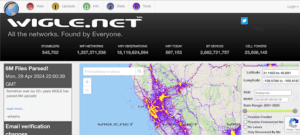
After signing up for an account, you can search for any SSIDs in any geological area and view details on each AP. If you are doing a wireless pen test, you can scope out the target location well in advance and plan your trip accordingly.
hcxtools and hashcat: Speed up your WiFi cracking
You may wish to crack WiFi passwords at a much faster speed and go through much bigger wordlists in less time (e.g., weakpass_3w specialized for WPA passwords), which can be achieved with the mighty power of modern GPUs that the aircrack-ng suite does not utilize. This is where hcxtools comes in; it can convert your capture files (e.g., from airodump-ng or bettercap) to hashes that can be used with hashcat to crack WPA/2 passwords much faster using available GPUs than aircrack-ng.
hcxtools can be installed on Kali via apt install hcxtools and Mac via brew install hcxtools.
To use it, simply specify the capture file (in pcap or pcapng format) and the desired location for an output hash file to hcxpcapngtool:
hcxpcapngtool ./wpa.full.cap -o test.22000
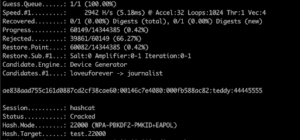
Now, test.22000 can be used with hashcat mode 22000 to crack WPA handshakes with a wordlist:
hashcat -m 22000 test.22000 /usr/share/wordlists/rockyou.txt
Wacker: WPA3 online cracking
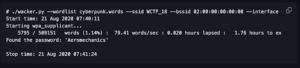
Wacker is one of the few operational tools that can be used to attack WPA3 APs. It allows you to use a wordlist to perform an online brute-force attack and repeatedly authenticate to an AP until the current password is found. A wordlist, target SSID, BSSID (which is the MAC address of the AP), the frequency of the AP’s channel, and an interface have to be specified to wacker when starting it, as the example shows:
./wacker.py --wordlist cyberpunk.words --ssid WCTF_18 --bssid 02:00:00:00:00:00 --interface wlan2 --freq 2412
The frequency of a 2.4 GHz WiFi channel can generally be calculated using the following formula:
2412 + 5 * ( 1 - channel number )
Or you can simply look it up in this article.
One limitation of this tool is that the source MAC address stays the same between attempts, so the APs could start blocking the attempts. This can be mitigated by constantly running macchanger, but the architecture of the tool, which uses wpa_supplicant, would cause the attack to slow further.
Wacker can be run simultaneously with multiple interface cards and wordlists in multiple terminal windows to speed things up:

Conclusion
From old classics to new toys, there are certainly many cool tools for hacking WiFi networks out there. However, at the time of writing this article, there is very limited research on WPA3 hacking; in fact, aside from denial-of-service and downgrade attacks to WPA2 and some implementation vulnerabilities, no design flaw in WPA3 password-protected setups has allowed the offline cracking of passwords and the decryption of traffic like in WPA2. You can learn more about WPA3 vulnerabilities from this talk. All in all, this means a thoroughly password-protected, firmware-patched WPA3 setup is pretty secure (as long as passwords are not easily guessable), and we should all transition our old WPA/2 networks to WPA3.