There is no doubt that the adoption of crowdsourced offensive security testing is growing. Organizations are recognizing the value of tapping into the power of hackers to build a security program that is more adaptable to security threats. Pen testing and bug bounty engagements are two of the biggest offensive security strategies. Previously, the question was, “which option is right for your organization?” However, more and more teams are opting for a combined approach.
Differences between pen testing and bug bounty engagements
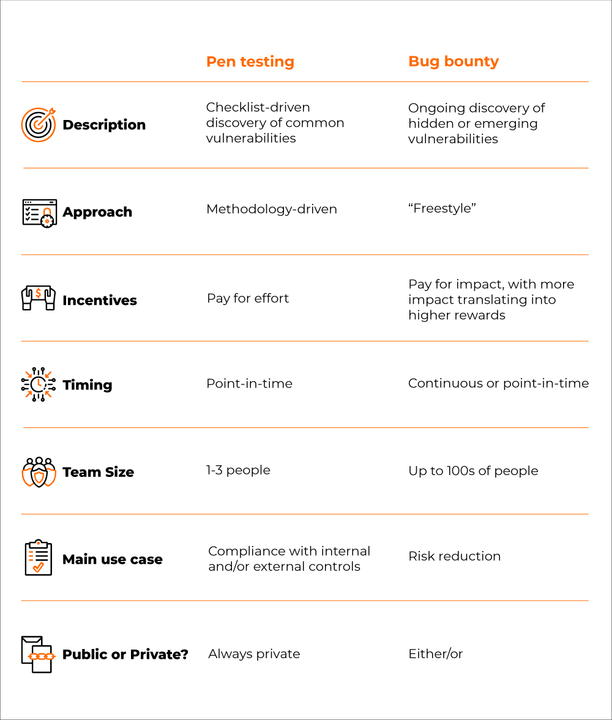
Let’s break down each offensive security strategy. Pen testing is a simulated cyberattack carried out by an authorized third party (known as pen testers) who tests and evaluates the security vulnerabilities of a target organization’s computer systems, networks, and application infrastructure. Pen tests are performed by external testers, are typically time bound, and usually follow a testing methodology. Generally, pen testing customers usually expect a final report after the engagement is complete that they can present to an auditor to demonstrate regulatory compliance.
Bug bounty engagements work by engaging with the global hacker community to find unknown vulnerabilities in your systems. This is done through a “pay for impact” economic model that incentivizes impactful results, meaning the more critical the vulnerability, the higher the reward.
Pen testing and bug bounty engagements have similar goals, but can have different levels of intensity of the assessment. Pen tests are fit for checklist-driven discovery of common vulnerabilities. Bug bounty engagements cover finding hidden flaws that pen tests might miss.
Reasons to combine pen testing and bug bounty engagements
Combining pen testing and bug bounty engagements into a single program with shared scope, integrations, credentials, and submissions is an effective way to achieve true risk reduction while addressing compliance needs. Here are three reasons why combining pen testing and bug bounty engagements is a best practice:
- Continuous protection—Combining solutions gives organizations the scale and agility needed to stay ahead of today’s biggest threats, like AI, and tomorrow’s unknown challenges.
- Solve for multiple needs—When bringing together the tried-and-true power of pen testing with the scale and efficiency of a bug bounty engagement, organizations solve for multiple needs while improving proactive threat detection.
- Get more high-impact results—Using these solutions together goes beyond compliance checklists and helps organizations find up to five times more high-impact vulnerabilities.
Introducing Max Pen Test
Max Pen Tests give you the best of both these worlds in a single package on the Bugcrowd Platform. In addition to delivering your auditor report, we’ll document prioritized vulnerabilities uncovered by tens or even hundreds of trusted testers specifically selected for their skill set, who are rewarded based on the impact of their results. Findings are viewable 24/7 in your dashboard, and if desired, flowed directly into DevSec workflows for fast remediation.
Unlike traditional time-boxed assessments, Max Pen Test engagements can also run continuously, in support of agile development cycles. As code is continuously updated, you’ll rest easier knowing your targets are being continuously assessed for new vulnerabilities.
The average Max Pen Test user finds 3-5x more high-impact vulnerabilities versus standard pen testing alone, which greatly reduces the cost per vulnerability.
Speak with an expert about Max Pen Test and see if it’s right for your organization.



