What is the Flipper Zero?

The Flipper Zero is a portable, multi-functional hacking device. It came out around the end of 2020, making quite a splash in the hacking community. It supports a range of wireless protocols and physical interfaces, and it also has a wide range of applications, from copying garage remotes to acting as a Bluetooth keyboard. Don’t let its cuteness fool you—it can be a dangerous hacking tool in the wrong hands. However, it can be an incredibly effective tool in the arsenal of someone who knows what to do with it. Hopefully by the end of this article, that could be you.
Disclaimer: Do not use the Flipper Zero to hack anything you do not have permission to! This article is for educational purposes only. Always refer to your local regulations for wireless frequencies.
Sub-Gigahertz radio hacking: Car keys, garage remotes, and more
First, let’s talk about the most powerful little chip that this hand-held device packs—the CC1101 wireless transceiver chip. This chip can transmit and receive the sub-1Ghz ISM band (a range of unlicensed frequencies for industrial, scientific, or medical use), it supports frequencies at 315/433/868/915 Mhz, and it can work up to 50 meters in range.

There’s a variety of protocols in this range, but the most common items you might find are garage door remotes and car keys. To scan any transmissions on this frequency, go into the Flipper’s Sub-GHz menu, and select “Read.” The little indicator light will start blinking rapidly, letting you know that it’s scanning nearby transmissions.
Once it has picked up a signal, it will automatically decode it. In that menu, you can choose to save the signal and replay it later in range of the door you wish to control—and watch that door open!
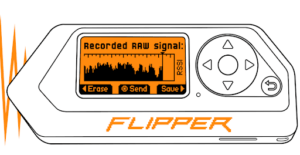
Often, there might be wireless protocols that the Flipper does not understand or support. This means that although it can capture the signal, it can’t decode it. This is why we always recommend using the “Read Raw” mode. This mode will read the raw signal, which you can save and then replay, or you can decode the raw signal offline when the protocol is supported later in a firmware update (or in alternative firmwares that support more protocols such as Unleashed and Xtreme).
Access card hacking: NFC and RFID
A second powerful use case of the Flipper Zero is its ability to read and write proximity access cards, such as hotel and gym cards, public transport cards, paywave credit cards, building access key fobs, and so on.
There are two general types of physical access cards: low frequency RFID (Radio Frequency Identification) cards (at 125kHz) and high frequency NFC (Near Field Communication) cards (13.56MHz). Within those frequencies, there are many different types of cards and protocols (languages that the cards communicate with). The Flipper Zero supports most of them.
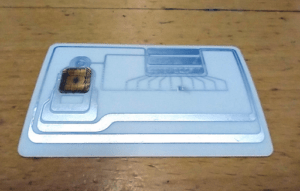
If you’ve ever held up a card to the light, or sliced one open across the middle, you’d see that they actually contain a microchip and long laid out pieces of wires that act as its circuit and antenna. This is because physical access cards are like mini computers. The reader/scanner uses RF energy to charge them up, and they perform some operation.
Generally speaking, the 125kHz cards are less secure because they lack the computing power to perform complex, secure encryption and simply spit out an ID number for authentication. In contrast, the 13.56MHz cards can support modern cryptography such as AES, or even run Java applications.

The Flipper Zero has separate application menus for RFID and NFC. To read 125 kHz RFID cards, go to the Flipper’s main menu -> 125 kHz RFID, then press “Read.” Place the card/key fob right underneath the flipper, and it will start decoding the data. This should only take a second. After reading, save the value and use the “Saved” menu in 125 kHz RFID to replay the same value back to a card reader. This time, the Flipper is acting as the card, not the reader.

With NFC cards, go to the main menu -> NFC instead. Here, you can choose to read a card and save it just like in RFID; however, there are cards that can’t be entirely saved because they have encrypted sections. Unlike RFID, where the card is authenticating to the reader using a value, with NFC the reader has to authenticate to the card with a key to decrypt its data, before performing actions based on the data that it’s read (such as open a door or “tap on” to public transport).
The only value that can be read without a key by the reader is the UID (unique identifier) of the card. Since we don’t have the key, the Flipper can try and guess it using a dictionary attack. If the card uses MIFARE Classic, it tries a list of default or known keys to authenticate each section of the card and attempt decryption. If that succeeds, the decrypted data will be saved to the Flipper. With more modern and secure protocols such as MIFARE DESFire, Flipper can’t decrypt the contents.
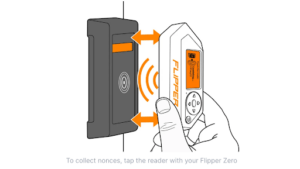
In NFC, you can also “Detect Reader” functionality.This can be used to mount the MFKey32 attack and deduce the key from the reader. Since each reader stores keys to authenticate to cards that it reads, this can be used to recover the key and successfully decrypt content on cards. Note that some readers use a key derived from the UID of the card. This means you can get the correct nonces (a nonce is a value that is used only once to prevent replay attacks) to crack the key for your card using the “Detect Reader” functionality after saving the card in reading mode without decrypting the sectors. You must use detect reader within the saved/read card, not the one in the main NFC menu. After getting the nonces from the reader with your card’s UID, launch the MFKey32 application to crack the found nonces from the reader, and then you can decrypt the card with the new found keys.
After saving a card successfully, you can emulate it from the “Saved” menu inside NFC. This allows you to authenticate to the reader and open doors with your saved cards.
Infrared: Hacking remote controls
The Flipper Zero also comes with a built-in IR (Infrared) sensor and transmitter; this allows you to use it to control devices such as TVs, air conditioners, projectors, fans, and so on. It has two main applications: copying remote control codes, or acting as a “universal remote” using a large database of saved actions (such as all remote control codes across TV brands for “power off”).
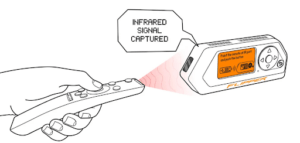
This process is very straightforward: within the main menu -> Infrared, click on “Learn New Remote” for the Flipper to start scanning for IR signals. Point your remote at the Flipper’s black spot on the side and press the button you’d like the Flipper to learn, and it will beep and learn it. Then it will appear in your “Saved Remotes” where you can replay the action.
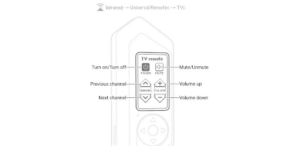
With the “Universal Remotes” menu within Infrared, you can select from a list of known device types (like TVs, Audio, Projectors, and so on) to get a nice remote control interface. From here, you can select actions for the Flipper to transmit. The Flipper will start transmitting IR codes from a large built-in database of actions. This will take a minute or two but eventually one of those codes will be recognized by the target device(s). Sometimes, this will have unintended consequences, as the “volume up” code for one TV brand might be the “next channel” code on another. The database of codes is non-exhaustive; when you don’t get it, you just have to get the read remote and learn the codes using the Flipper.
Bluetooth shenanigans: Remote bad USB attacks
The Flipper Zero comes with a built-in Bluetooth chip, as well as a companion mobile app that can connect via Bluetooth to perform things like remote screen control, update firmware, access files, and so on. But the coolest use case of its Bluetooth chip is that we can use the Flipper as a Bluetooth HID (Human Interface Device), such as acting as a keyboard or a mouse.
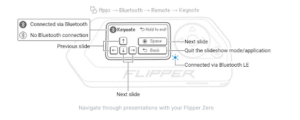
The stock (default) firmware has a Bluetooth Remote app that can be used in many modes, from a Keynote remote to a Mouse Jiggler. These create easy to use interfaces for specific use cases.
What if we want more? For example, the stock firmware comes with a “Bad USB” app that can inject keystrokes into a connected computer using HAK5 USB Rubber Ducky style payloads. This could be used during a pentest to quickly fire a reverse shell from an unlocked computer. With a custom firmware such as the Xtreme Firmware, we can use the Flipper to act as a new Bluetooth keyboard to inject keystrokes, as well as try to mimic an existing Bluetooth device by copying its name and MAC address.
Below is an example payload for Windows that will open the Command Prompt. Put the commands in a popcmd.txt file under /badkb directory in the SD card, and load up the Bad KB app inside the Xtreme firmware to fire it:
REM wait a second
DELAY 1000
REM open windows+R
GUI r
DELAY 500
STRING cmd
DELAY 500
ENTER
You can find a large repository of Flipper Zero USB payloads here for testing real-world attacks, either via a USB cable or Bluetooth.
GPIO expansions and WiFi hacking
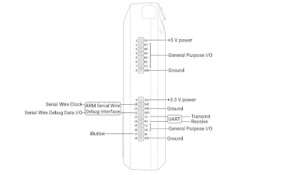
The Flipper Zero also comes with a set of GPIO ports at the top, allowing general purpose input/output interactions when wired to different interfaces or modules. Classic use cases include USB serial terminals, using the flipper as a power source in custom LED circuits, interacting with the I2C protocol and so on.
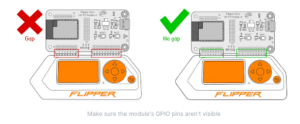
These GPIO ports are also designed to allow expansion modules or addons for the Flipper, such as the WiFi Devboard and Video Game Module. After insertion, apps in the Flipper firmware that support the module can be used, like the WiFi Marauder app which allows you to sniff nearby WiFi traffic and send deauthentication packets, saving pcaps and logs to the SD card.
Conclusion
We’ve covered most of the hacky features of the Flipper Zero in this blog, but that’s just the tip of the iceberg. With some C knowledge, you can even compile your own version of the firmware or write your first Flipper app. This versatile device will no doubt aid you on your journey to hacking all the things, from IoT appliances to industrial equipment.
Happy hacking!



