The historic Log4j RCE vulnerability was discovered on approximately Dec. 9, 2021, and many security teams continue to grapple with it. It’s another reminder (as if we needed one) that cybersecurity is a team sport that requires intense, continuous collaboration with ethical hackers and security researchers outside your organization. Automated solutions have their place, but they’re no substitute for human diversity and ingenuity applied at scale for finding hidden vulnerabilities across complex software supply chains.
At Bugcrowd, we believe the value of our platform goes well beyond its role as a technology framework for collaborating with ethical hackers and security researchers. Its ability to separate signal from noise through meticulous, rapid triage, and to provide prioritization and remediation recommendations based on past experiences, are just as critical.
Rapid Response at Scale
The Log4j incident is a perfect illustration of this fact. Consider that:
- To date, ethical hackers and security researchers worldwide have submitted more than 1,200 raw Log4j-related reports on the Bugcrowd Security Knowledge Platform, and 500+ of those were validated, triaged/prioritized, and passed on to customers for remediation by Bugcrowd (the remainder turning out to be duplicates, false positives, or otherwise invalid).
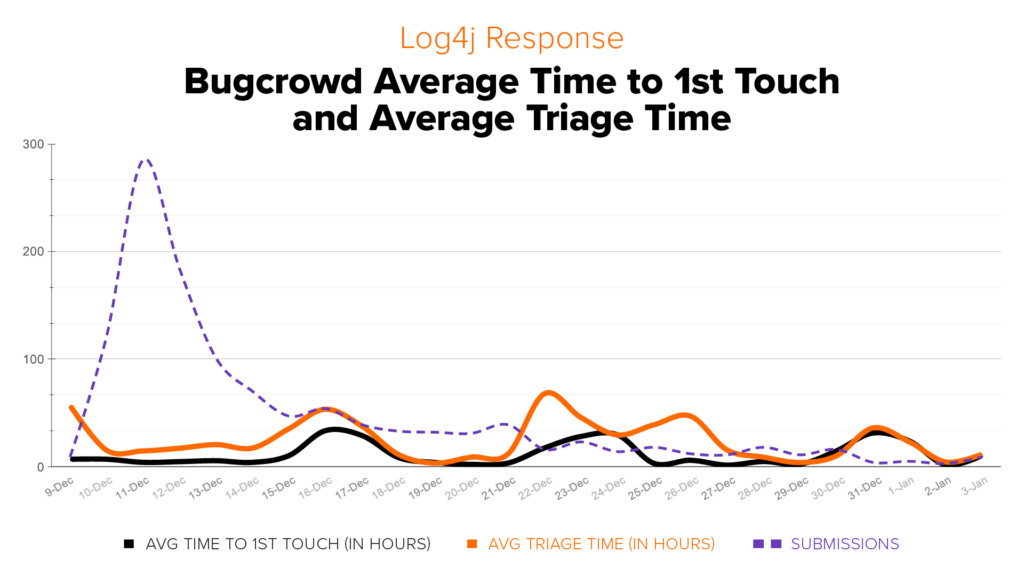
- Activity on the Bugcrowd platform started to spike on December 9 and peaked on December 11, with nearly 300 submissions on that date.
- During that critical period and beyond, most Log4j issues were validated, triaged, prioritized, and accepted/payout approved to the researcher in well under a single business day (even accounting for nights and weekends) under the stress of skyrocketing scale–with one $90,000 payout for a particularly impactful bug. Most P1s, initially including a proof of concept beyond a DNS pingback response, were handled in under three hours. And keep in mind that this activity was incremental to the thousands of other vulnerability reports the Bugcrowd platform processes daily.
- Even with this surge, response times were maintained across the holidays to ensure quick visibility into Log4j-related issues for customers.
Platform Power
The key to our rapid response time is the Bugcrowd Security Knowledge Platform–a unique blend of technology, data, and human intelligence. Rather than treating validation and triage as a check box or afterthought, we consider it an integral part of the platform and a critical ingredient for customer success. For that reason, the Bugcrowd platform orchestrates and streamlines triage-related workflows for security researchers, customers, and our own Security Engineering team alike.
Through the platform, Bugcrowd’s globally distributed team of 40+ Security Engineers also have access to data collected over a decade of building 1000s of customer solutions that informs how vulnerabilities are validated, triaged, and remediated. The result is super-fast triage (meeting internal SLOs more than 99% of the time) and actionable remediation advice enhanced with contextual intelligence for customers like Atlassian, Netflix, Tesla, and Twilio.
Learn more about the Log4j vulnerability/Log4Shell exploit and Bugcrowd’s response here. To learn more about the Bugcrowd approach to validation and triage, download this product sheet.



